Step-by-Step Guide: Building a Highly Available Container Registry with Amazon ECR and Integrating it with AWS EKS
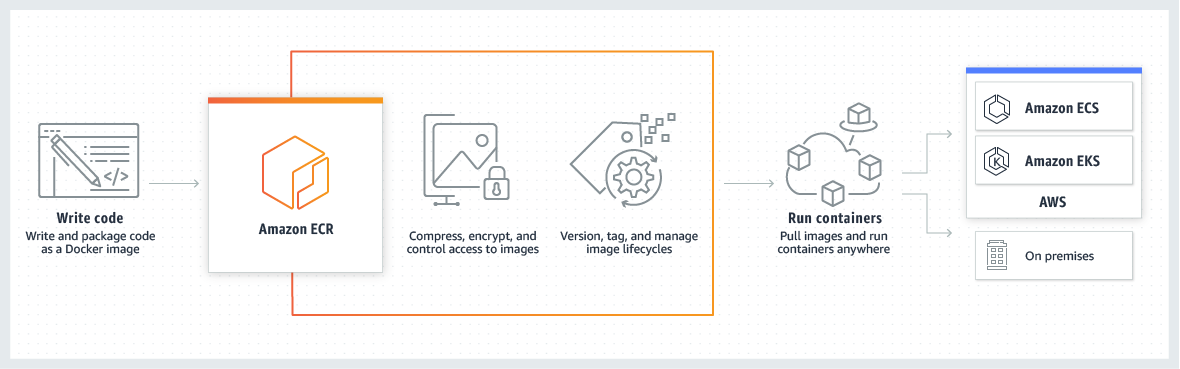 |
| AWS ECR |
Introduction:
Building a highly available container registry is crucial for businesses adopting containerized applications. Amazon Elastic Container Registry (ECR) offers a reliable and scalable solution for storing and managing container images, while Amazon Elastic Kubernetes Service (EKS) provides a powerful container orchestration platform. In this step-by-step guide, we will walk you through the process of setting up a highly available container registry with Amazon ECR and integrating it with AWS EKS. By following these steps, businesses can leverage the benefits of a robust container registry and seamlessly deploy applications on EKS.
Step 1: Set Up an Amazon ECR Repository
1. Log in to the AWS Management Console and navigate to the Amazon ECR service.
2. Click on "Create repository" to create a new repository.
3. Provide a name for the repository and configure repository policies to control access and permissions.
4. Choose the region where you want to create the repository and click "Create repository" to complete the setup.
Step 2: Enable Replication for High Availability
1. In the ECR console, select the repository you created in Step 1.
2. Click on the "Replication" tab and choose "Configure replication."
3. Enable replication and select the target region(s) where you want to replicate your container images.
4. Configure replication settings, such as image tag immutability and the number of images to replicate.
5. Save the replication configuration.
Step 3: Configure AWS EKS Cluster
1. Set up an Amazon EKS cluster using the AWS Management Console or AWS CLI.
2. Configure the necessary parameters, such as the cluster name, networking, and IAM roles.
3. Follow the AWS documentation for detailed instructions on setting up an EKS cluster.
Step 4: Authenticate EKS Cluster with ECR
1. Open the AWS Management Console and navigate to the EKS service.
2. Select your EKS cluster and click on "Configuration" in the navigation panel.
3. Locate the "Permissions" section and click on "Add or edit permissions."
4. Update the cluster's access permissions by adding the necessary policies for ECR access.
5. Save the changes to apply the updated permissions.
Step 5: Deploy Containerized Applications on EKS
1. Build your containerized application using a Dockerfile and push the image to your Amazon ECR repository.
2. Connect to your EKS cluster using the AWS CLI or the Kubernetes command-line tool, kubectl.
3. Create a Kubernetes deployment manifest file defining the desired state of your application.
4. Deploy the application to the EKS cluster using the kubectl command.
5. Monitor the deployment status and validate the successful deployment of your containerized application.
Step 6: Implement Security Measures
1. Enable encryption at rest for your ECR repository to protect container images.
2. Set up appropriate IAM roles and policies to manage access control and permissions for repository users.
3. Leverage ECR's image vulnerability scanning to identify and remediate any security vulnerabilities in your container images.
Step 7: Test and Scale your application
1. Perform thorough testing of your containerized application running on the EKS cluster.
2. Use the scaling capabilities of EKS to adjust the number of running instances based on demand.
3. Monitor the performance and scalability of your application using AWS CloudWatch and other monitoring tools.
Conclusion:
By following this step-by-step guide, businesses can build a highly available container registry with Amazon ECR and seamlessly integrate it with AWS EKS. This enables businesses to store, manage, and deploy container images efficiently while leveraging the scalability and robustness of EKS for their applications.
The combined power of ECR and EKS empowers businesses to accelerate their container-based initiatives, ensure high availability, and drive innovation in their cloud-native ecosystem.
Comments
Post a Comment